Libvirt Xml Serial Console
Virt-install is a command line tool for creating new KVM, Xen, or Linux container guests using the 'libvirt' hypervisor management library. See the EXAMPLES section at the end of this document to quickly get started. Virt-install tool supports both text based & graphical installations, using VNC or SDL graphics, or a text serial console. The guest can be configured to use one or more virtual.
Virt-install is a command line tool for creating new KVM, Xen, or Linux container guests using the 'libvirt' hypervisormanagement library. See the EXAMPLES section at the end of this document to quickly get started.virt-install tool supports both text based & graphical installations, using VNC or SDL graphics, or a text serialconsole. The guest can be configured to use one or more virtual disks, network interfaces, audio devices, physical USB or PCIdevices, among others.The installation media can be held locally or remotely on NFS, HTTP, FTP servers. In the latter case'virt-install' will fetch the minimal files necessary to kick off the installation process, allowing the guest to fetch the rest of theOS distribution as needed. PXE booting, and importing an existing disk image (thus skipping the install phase) are alsosupported.Given suitable command line arguments, 'virt-install' is capable of running completely unattended, with the guest 'kickstarting' itself too.
Thisallows for easy automation of guest installs. An interactive mode is also available with the -prompt option, but this will only ask for the minimum requiredoptions.OptionsMost options are not required.
Minimum requirements are -name, -ram, guest storage (-disk, -filesystem or -nodisks), and an install option.-h, -helpShow the help message and exit-connect=CONNECTConnect to a non-default hypervisor. The default connection is chosen based on the following rules:xenIf running on a host with the Xen kernel (checks against /proc/xen)qemu:///systemIf running on a bare metal kernel as root (needed for KVM installs)qemu:///sessionIf running on a bare metal kernel as non-rootIt is only necessary to provide the '-connect' argument if this default prioritization is incorrect, eg if wanting to use QEMUwhile on a Xen kernel.General Options General configuration parameters that apply to all types of guest installs.-n NAME, -name=NAMEName of the new guest virtual machine instance.
This must be unique amongst all guests known to the hypervisor on the connection, including those notcurrently active. To re-define an existing guest, use the (1) tool to shut it down ('virsh shutdown') & delete ('virsh undefine') it prior torunning 'virt-install'.-r MEMORY, -ram=MEMORYMemory to allocate for guest instance in megabytes. If the hypervisor does not have enough free memory, it is usual for it to automatically take memory awayfrom the host operating system to satisfy this allocation.-arch=ARCHRequest a non-native CPU architecture for the guest virtual machine. If omitted, the host CPU architecture will be used in theguest.-machine=MACHINEThe machine type to emulate.
This will typically not need to be specified for Xen or KVM, but is useful for choosing machine types of moreexotic architectures.-u UUID, -uuid=UUIDUUID for the guest; if none is given a random UUID will be generated. If you specify UUID, you should use a32-digit hexadecimal number. UUID are intended to be unique across the entire data center, and indeed world. Bear this in mind if manuallyspecifying a UUID -vcpus=VCPUS,maxvcpus=MAX,sockets=#,cores=#,threads=#Number of virtual cpus to configure for the guest. If 'maxvcpus' is specified, the guest will be able to hotplug up to MAX vcpus while theguest is running, but will startup with VCPUS.CPU topology can additionally be specified with sockets, cores, and threads. If values are omitted, the rest will be autofilled preferingsockets over cores over threads.-cpuset=CPUSETSet which physical cpus the guest can use.
'CPUSET' is a comma separated list of numbers, which can also be specified in ranges or cpus to exclude.Example:0,2,3,5: Use processors 0,2,3 and 51-5,^3,8: Use processors 1,2,4,5 and 8If the value 'auto' is passed, virt-install attempts to automatically determine an optimal cpu pinning using NUMA data, if available.-numatune=NODESET,mode=MODETune NUMA policy for the domain process. Example invocations-numatune 1,2,3,4-7-numatune '1-3,5',mode=preferredSpecifies the numa nodes to allocate memory from. This has the same syntax as '-cpuset' option. Mode can be one of 'interleave', 'preferred', or'strict' (the default). See 'man 8 numactl' for information about each mode.The nodeset string must use escaped-quotes if specifying any other option.-cpu MODEL,+feature,-feature,match=MATCH,vendor=VENDORConfigure the CPU model and CPU features exposed to the guest.
The only required value is MODEL, which is avalid CPU model as listed in libvirt's cpumap.xml file.Specific CPU features can be specified in a number of ways: using one of libvirt's feature policy values force, require, optional, disable,or forbid, or with the shorthand '+feature' and '-feature', which equal 'force=feature' and 'disable=feature' respectivelySome examples:-cpu core2duo,+x2apic,disable=vmx Expose the core2duo CPU model, force enable x2apic, but do not expose vmx-cpu host Expose the host CPUs configuration to the guest. This enables the guest to take advantage of many of the host CPUs features (better performance), but maycause issues if migrating the guest to a host without an identical CPU.-descriptionHuman readable text description of the virtual machine. This will be stored in the guests XML configuration for access by otherapplications.-security type=TYPE,label=LABEL,relabel=yes noConfigure domain security driver settings. Type can be either 'static' or 'dynamic'. 'static' configuration requires a security LABEL.Specifying LABEL without TYPE implies static configuration.
To have libvirt automatically apply your static label, you mustspecify relabel=yes.Installation Method options -c CDROM, -cdrom=CDROMFile or device use as a virtual CD-ROM device for fully virtualized guests. It can be path to an ISO image, or to a CDROMdevice. It can also be a URL from which to fetch/access a minimal boot ISO image. The URLs take the same format as described forthe '-location' argument. If a cdrom has been specified via the '-disk' option, and neither '-cdrom' nor any other install optionis specified, the '-disk' cdrom is used as the install media.-l LOCATION, -location=LOCATIONDistribution tree installtion source. Virt-install can recognize certain distribution trees and fetches a bootable kernel/initrd pair to launch the install.With libvirt 0.9.4 or later, network URL installs work for remote connections. Virt-install will download kernel/initrd to the local machine,and then upload the media to the remote host.
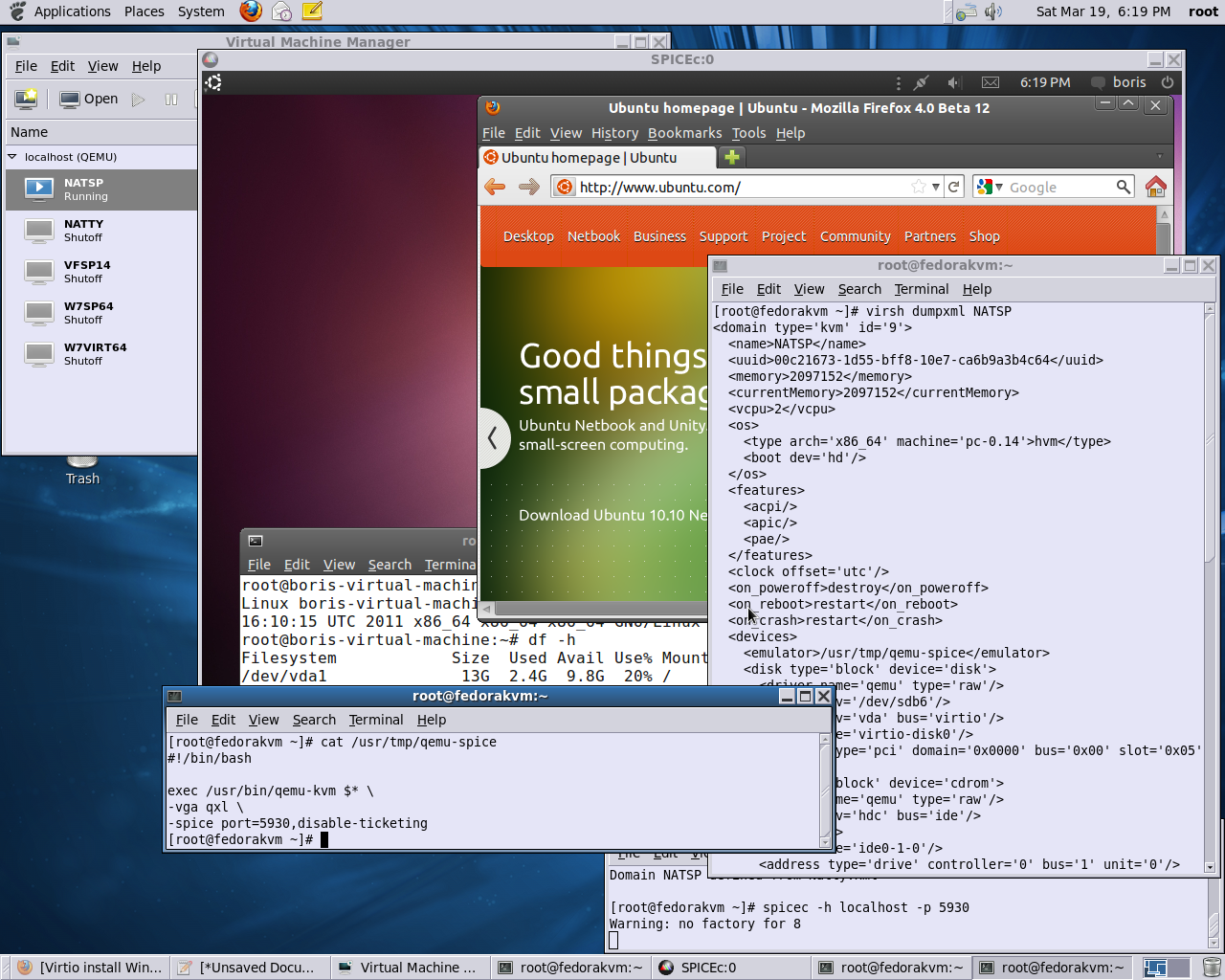
I have a serial console working for a centos7 guest without graphics, which I access with virsh console vm. I frequently use multiple 'consoles' on my VMs - one for an interactive console showing the boot-up and ending with a login prompt, and another to log all of that to a text file (usually /var/lib/libvirt/consoles/.log)I don't know if you can have multiple interactive 'consoles' in a VM, but you can add as many serial ports as you like, and then run getty on them in the VM for the login prompt.These serial ports in the VM can be connected to, e.g., a file, or a socket, or a TCP port on the host that speaks telnet protocol.
Easiest to work with is probably a telnet port.e.g. To add a serial ttyS1 serial port which can be accessed via telnet, save the following XML fragment to /tmp/serial1.xml: Then run virsh attach-device -config /tmp/serial1.xml.That will add a serial port device to the VM, which will be activated the next time the VM restarts. (There may be some way to add it as a hot-pluggable USB device rather than a non-USB serial port, and avoid the need to restart the VM.
I've never cared enough to find out).After the VM has rebooted, run a getty on the port. With sysvinit, edit /etc/inittab and run telinit q.With systemd: systemctl enable getty@ttyS1.servicesystemctl start getty@ttyS1.serviceTo connect to the VM's serial port from the KVM host, run telnet 127.0.0.1 4555.You can create as many serial ports as you like, each listening on a different port.